
Tech & Sci
12:26, 28-Jun-2017
More countries hit by 'Petya' ransomware
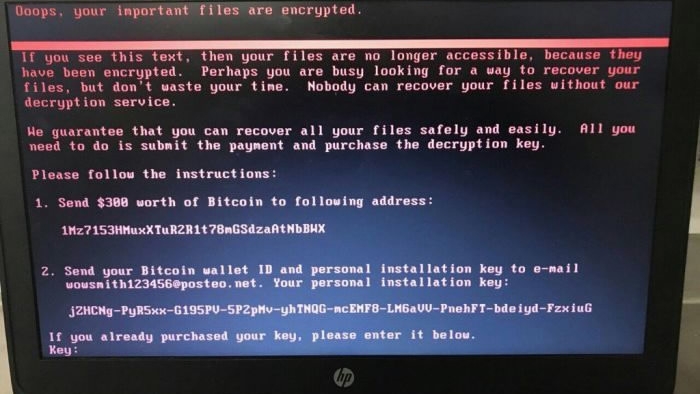
A new global cyber attack on Tuesday hit a handful of countries, including the UK, Russia, Ukraine, the US, Norway, France, Finland, Denmark, Germany, India and Australia, disrupting the work of government departments and affecting businesses.
The total number of attacks is not immediately clear.
The ransomware, identified at first as "Petya," which started circulating last year, now appears to be an offshoot of "Petya" with many budding it "NotPetya". It reportedly disrupted computers with a virus similar to that of WannaCry, which infected more than 300,000 devices last month.
It included a code known as "Eternal Blue," which cyber security experts widely believe was stolen from the US National Security Agency (NSA) and was also used in WannaCry.
A computer screen displays a cyber attack notice reportedly holding computer files for ransom on Tuesday in Kiev, Ukraine. / AP Photo
A computer screen displays a cyber attack notice reportedly holding computer files for ransom on Tuesday in Kiev, Ukraine. / AP Photo
Computer security specialists said that the cryptolocker exploited an already patched vulnerability in Windows software by encrypting hard drives and overwriting files, and then demanded 300 US dollars in bitcoin to restore access. Since the encrypting program was not named, finding a solution would be very difficult.
Ukraine was the first to report serious intrusions of the country's power grid as well as at banks and government offices, where one senior executive posted a photo of a darkened computer screen and the words, "the whole network is down."
It appears the country is the primary target.
Russia's largest oil company Rosneft also reported falling victim to hacking, following Ukraine, as well as Danish shipping giant Moller-Maersk, Britain's biggest advertising and marketing agency WPP and US drug giant Merck.
More than 30 victims paid into the bitcoin account associated with the attack, according to a public ledger of transactions listed on blockchain.info.
Countries scramble for remedy
Experts said they expected the impact to be smaller than WannaCry since many computers had been patched with Windows updates in the wake of last month's attack. Companies that had been attacked said they are investigating the cause and taking steps to remedy the issue.
Microsoft said its anti-virus software can detect and remove the ransomware used in the latest attack, and noted it is continuing to look into the latest cyber attack and will take necessary steps to protect customers.
Ukrainian Prime Minister Volodymyr Groysman wrote on Facebook that "it was an unprecedented attack, but our IT-experts are doing their job and protecting critical infrastructure. Important systems have not been affected."
The US Department of Homeland Security said it was monitoring the attacks and coordinating with other countries. It advised victims not to pay the extortion, saying that doing so does not guarantee access will be restored.

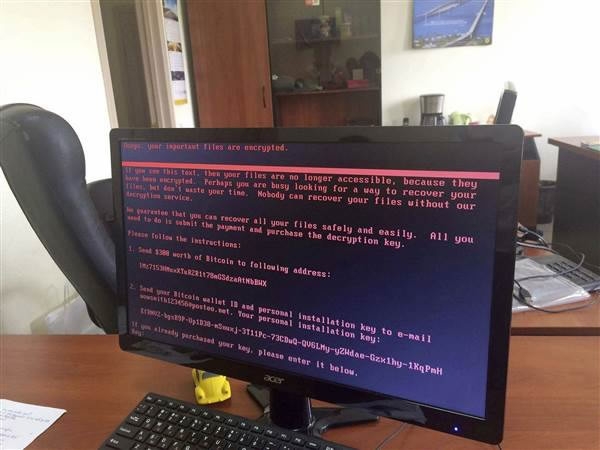
Message by Petya ransomware on a bank terminal. /Reuters Photo
Message by Petya ransomware on a bank terminal. /Reuters Photo
Australian Cyber Security Minister Dan Tehan said the attack was "a wake-up call to all Australian businesses to regularly back up their data and install the latest security patches".
Although China has not seen traces of "Petya," it did suffer from WannyCry in May which had paralyzed online payment systems at petrol stations across the country and invaded colleges to encrypt papers and other documents.
The Chinese government released on Tuesday an emergency response plan for Internet security incidents, in which serious cases will trigger measures including establishment of emergency headquarters, 24-hour monitoring and multi-department coordination in handling the aftermath.

A supermarket hit by a cyber attack on June 27, 2017. /Reuters Photo
A supermarket hit by a cyber attack on June 27, 2017. /Reuters Photo
Previous attacks and global trend
The Baltic nation of Estonia was the first state hit by a massive cyber attack in 2007, which paralyzed key corporate and government web services for days. Estonia blamed Moscow, with which it was mired in a diplomatic conflict, but Moscow denied the charge.
A year later, in 2008, Georgia suffered similar attacks, also during a conflict with Russia.
In July 2009, the White House, Pentagon and State Department websites were targeted in a coordinated cyber attack which also struck sites in South Korea. Washington blamed Pyongyang for the hacking, a claim which it denied.
In January 2015, a group declaring support for ISIL hacked into the social media accounts of US Central Command, causing an embarrassing setback for Washington in its war against the terrorist group in Syria and Iraq.
Major companies and media houses have also been targeted, including Yahoo!, which was targeted by hackers seeking personal data on millions of users in both 2013 and 2014.
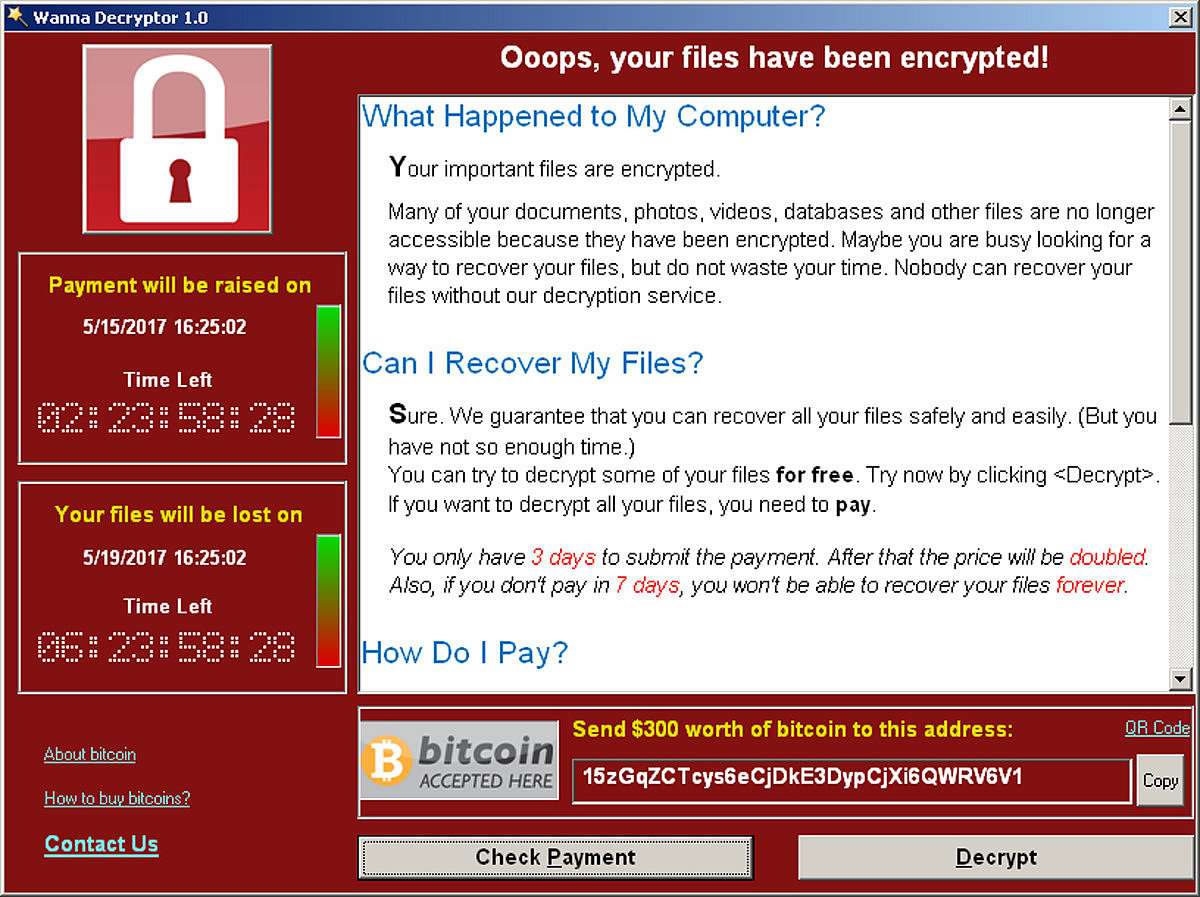
The WannaCry ransomware broke out in May. /VCG Photo
The WannaCry ransomware broke out in May. /VCG Photo
Tagged by EU's law enforcement agency as "unprecedented", WannaCry is the world's largest cyber attack ever seen, in which it made hundreds of organizations in 150 countries its preys.
From "cyberwar" to "hacktivism" and "cyberterrorism," it is obvious that the growing number and increasing scale of cyber attacks are not only linked with companies' consistent overlook of system flaws, but also tied to some political factors.
(Source: Agencies)
Related stories:

SITEMAP
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3