
Tech & Sci
16:50, 09-Dec-2018
Police arrest hacker behind WeChat ransomware attack
Updated
16:00, 12-Dec-2018
By Yu Yiwei

Authorities in south China's Guangdong Province have arrested a man who has been suspected of developing ransomware that has spread to over 100,000 computers in China.
Police arrested a 22-year-old male surnamed Luo in the city of Dongguan on December 5.
Chinese cybersecurity firm Huorong Security discovered the ransomware on December, and identified it as a type of supply chain attack.
The virus was first implanted in the Chinese programming software "Easy Programming Language" used by many application developers, which means products made by those developers using that software would contain that malicious virus.
According to a report released by Huorong Security, over 50 software programs were injected with the ransomware. Once computer users install any of these applications, all files on the computers would be encrypted except for those with the extensions gif, exe, and temp.
The ransomware also lifted the account and password data of almost 50,000 users from Taobao, Tmall, Alipay, Baidu Cloud, 163 email service, and JD.com.
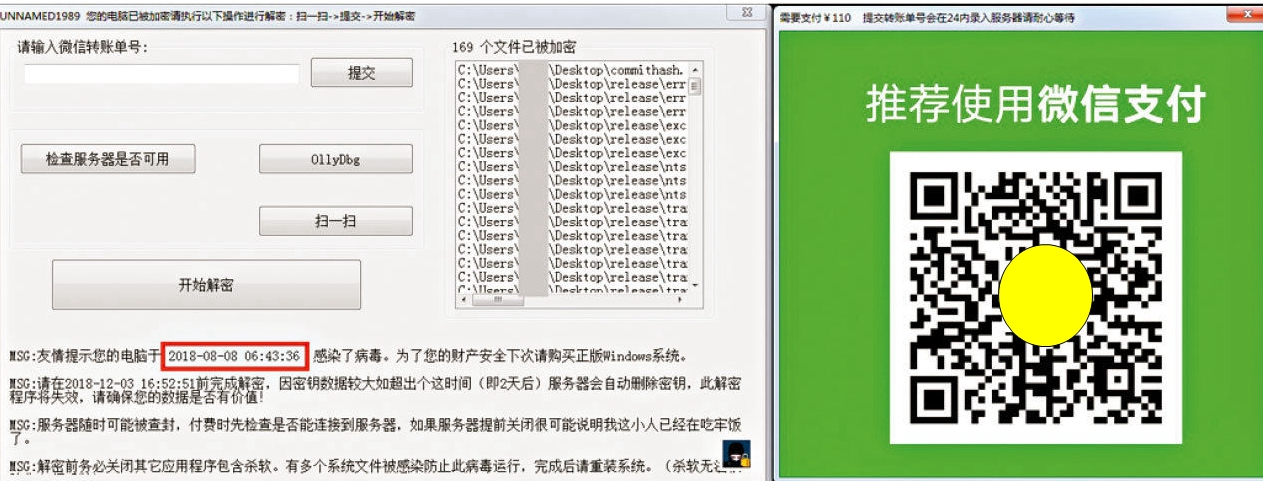
The hacker asked victims to pay 110 yuan via WeChat payment service.
The hacker asked victims to pay 110 yuan via WeChat payment service.
Interestingly, instead of demanding ransom payments in bitcoin, which can mask user identities, the hacker asked victims to pay 110 yuan (nearly 16 U.S. dollars) within three days by scanning a WeChat QR code to have their data unlocked.
Since the QR code is linked to a personal account, WeChat cybersecurity experts were soon able to identify the hacker.
Moreover, Huorong Security researchers also traced his personal information and handed over his name and phone number to the police.
Computer users who have been affected by the ransomware don't need to worry too much. Cybersecurity agencies such as Tencent PC Manager and Huorong Security said that the ransomware has been successfully cracked, and they have already released software to weed out the virus.
(Top image via VCG)

SITEMAP
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3