
Opinion
16:18, 26-Jan-2019
Security risks behind #10YearChallenge
Li Zheng

Editor's note: Li Zheng is an associate research fellow at the China Institutes of Contemporary International Relations, Institute of American Studies and the director of the American Security Center, Institute of American Studies. The article reflects the author's opinion, and not necessarily the views of CGTN.
In the past weeks, a meme called "10-year Challenge" has become popular on Facebook. It encourages people to post two photos of themselves side-by-side — one from today and another from a decade ago — to show how they've changed in the appearance.
The social media "task" has attracted millions of participants, including Facebook founder Mark Zuckerberg and several Hollywood stars. For most participants, this is the first time they've uploaded their photos from 10 years ago. Mobile and digital cameras were not popular then, so they need to convert their photos to a digital format before uploading. As the number of participants increases, some observers have begun to question the motives behind the activity and express their concerns about the social risks of uploading old photos.
Some believe that the intention behind this activity is to train Facebook's face recognition artificial intelligence. Traditional artificial intelligence can only rely on the identification of photos to carry out training, which makes it difficult to judge the influence of natural aging on facial features.
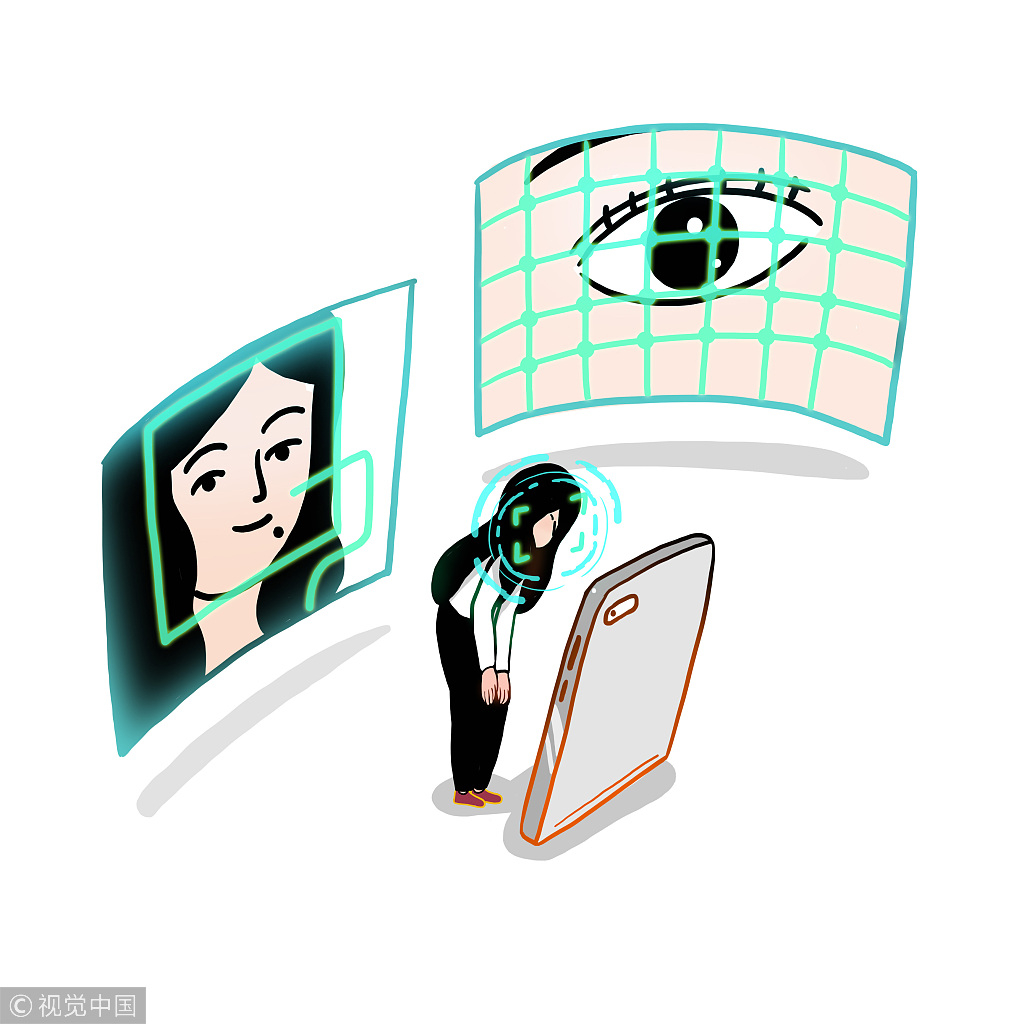
Image recognition artificial intelligence. /VCG Photo
Image recognition artificial intelligence. /VCG Photo
By comparing photos from 10 years ago and now, Facebook can collect a lot of useful material, which significantly improves the accuracy of face recognition. The photo uploading could also be risky as some old photos are likely to be stolen and could be used to create fake social media accounts for conducting frauds.
These concerns stem from the international community's uneasiness about the protection of personal information. U.S. Internet giants such as Google, Apple, Facebook, Amazon, and Netflix cover users' online and offline lives which include their travel routes, aesthetic preferences, and consumption habits.
The "10-year challenge" is not the only social media activity that has raised concerns. In July 2018, Google launched a game called "Cai Hua Xiao Ge" on Chinese social media. In this game, users needed to interact with Google's artificial intelligence to draw a sketch that allows Google to recognize their facial features.
According to reports, the game collected more than 50 million sets of data, which not only helped Google improve its AI capabilities in image recognition but also to keep a record of users' brushstrokes and writing habits. Such data could be stolen and used for fake signatures.
Today, U.S. Internet giants have entered a stage of high monopoly. Their tentacles extend to the real world and the desire to collect data goes deeper. These companies are no longer satisfied with collecting data on users' online activities and encourage users to provide old data that was not digitized earlier in multiple ways.
This data will be analyzed by artificial intelligence to identify users and understand the deep psychology of users, which could be used to affect their behavior and choices.
In the 2016 U.S. election, a company called Cambridge Analytica used Facebook users' data to deliver accurate fake news and political advertising to millions of American voters, likely to affect election results. If such data is used to launch psychological or information warfare against other countries, it may exert a catastrophic impact on a country's social stability.

VCG Photo
VCG Photo
A new competition between U.S. Internet giants and the governments is emerging in international politics. Internet giants use developing technology to snatch users' data and limit their freedom to choose, while governments implement ever-improving regulations to constrain these companies.
In this competition, developing countries are in a weak position as they lack corresponding technical abilities to judge the true intentions of these technology giants, they often adopt stricter Internet supervision methods and place high importance on the concept of cyber sovereignty. China's regulation in the Internet field is based on this basic idea.
Cyber sovereignty does not mean data closure and protection of the domestic Internet market. Its core lies in respecting the differences in the governance of various countries and does not impose other's governance concepts as an additional condition for bilateral relations.
China welcomes U.S. Internet giants to enter the Chinese market, but only if they comply with the Chinese legal system. When U.S. Internet companies operate similar activities in China, they should indicate their true intentions and fully protect the security and privacy of data.
(If you want to contribute and have specific expertise, please contact us at opinions@cgtn.com.)

SITEMAP
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3