
Tech & Sci
10:44, 20-Jun-2017
Nearly 200 mln US voters' personal info leaked by GOP

More than 198 million US citizens' personal information was accidentally exposed by a marketing firm that collects data for the Republican National Committee this week, making it the largest leak incident of voter records in American history.
Deep Root Analytics – one of the three contracted to work for the conservatives during last year's presidential campaign – stored these sensitive documents on a publicly accessible Amazon server, which was later found by Chris Vickery, an analyst working for the cybersecurity firm UpGuard, on June 12.
Representing 60 percent of the US population, the data revealed contains the voters' home addresses, birthdates and phone numbers besides political preferences that assist analysts predict how individual voter would react to hot topics such as gun ownership, stem cell research and abortion rights etc.
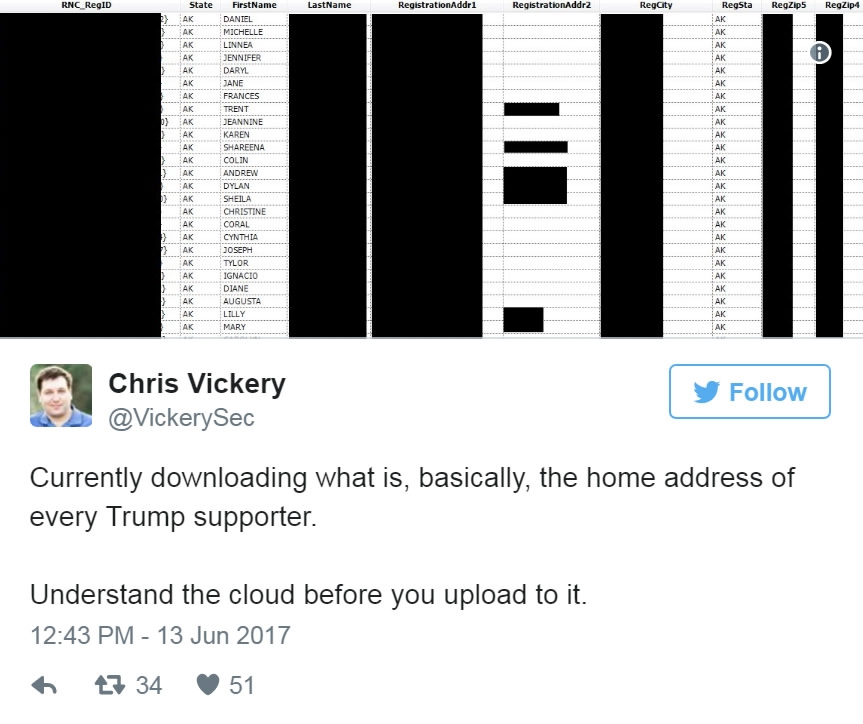
Twitter Photo
Twitter Photo
More than a terabyte of the information leaked was not password protected, said UpGuard, and part of the data pool was contributed by outside sources such as the super PACs and Reddit. One subreddit called r/fatpeoplehate is now banned.
The GOP paid Deep Root almost a million dollars during US President Donald Trump's campaign, according to Federal Election Commission reports. What the company mainly does involves identifying audiences for political advertisements.
The exposure was believed to occur when Deep Root was updating its security settings early this month, and they have already sought a cybersecurity firm to help investigate the issue.

Trump supporters celebrate the president's birthday in front of Trump Tower on June 14, 2017 in New York City. /VCG Photo
Trump supporters celebrate the president's birthday in front of Trump Tower on June 14, 2017 in New York City. /VCG Photo
In a statement, Deep Root said, "Since this event has come to our attention, we have updated the access settings and put protocols in place to prevent further access."
Although Deep Root insisted that they did not experience any malicious access to the data by a third party during the last 12 days it was exposed, some experts are still concerned about who may have accessed them before it became known to the public.
"While the scale and significance of this data exposure is nearly unprecedented, misconfigurations of the type that rendered the database public are not. With cyber risk increasingly endemic on all digital platforms, this exposure is a reminder that we must all begin fostering cyber resilience, or risk a future of these kinds of breaches," said UpGuard in a statement.
11159km

SITEMAP
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3
Copyright © 2018 CGTN. Beijing ICP prepared NO.16065310-3