
China on Tuesday released an investigative report to disclose details of cyberattacks on a Chinese university launched by the U.S. National Security Agency (NSA), indicating that the sniffing and stealing cyber weapon "Suctionchar" is one of the most direct culprits that led to the theft of a large amount of sensitive data.
The report was released by China's National Computer Virus Emergency Response Center (CVERC) in collaboration with cybersecurity company Beijing Qi'an Pangu Laboratory Technology Co., Ltd.
According to CVERC, the NSA-affiliated Tailored Access Operations (TAO) Office used 41 types of cyber weapons in the exposed cyber attacks against China's Northwestern Polytechnical University (NPU). The NSA conducted over 10,000 cyberattacks against China in recent years and is suspected to have stolen 140 gigabytes of valuable data, according to a report released on September 5 by CVERC and internet security company Qihoo 360 Technology Co. Ltd.
Furthermore, traces of "Suctionchar" have been found in the networks of other institutes besides the NPU, which means that the NSA may have carried out a large-scale cyberattack against China, according to Tuesday's report.
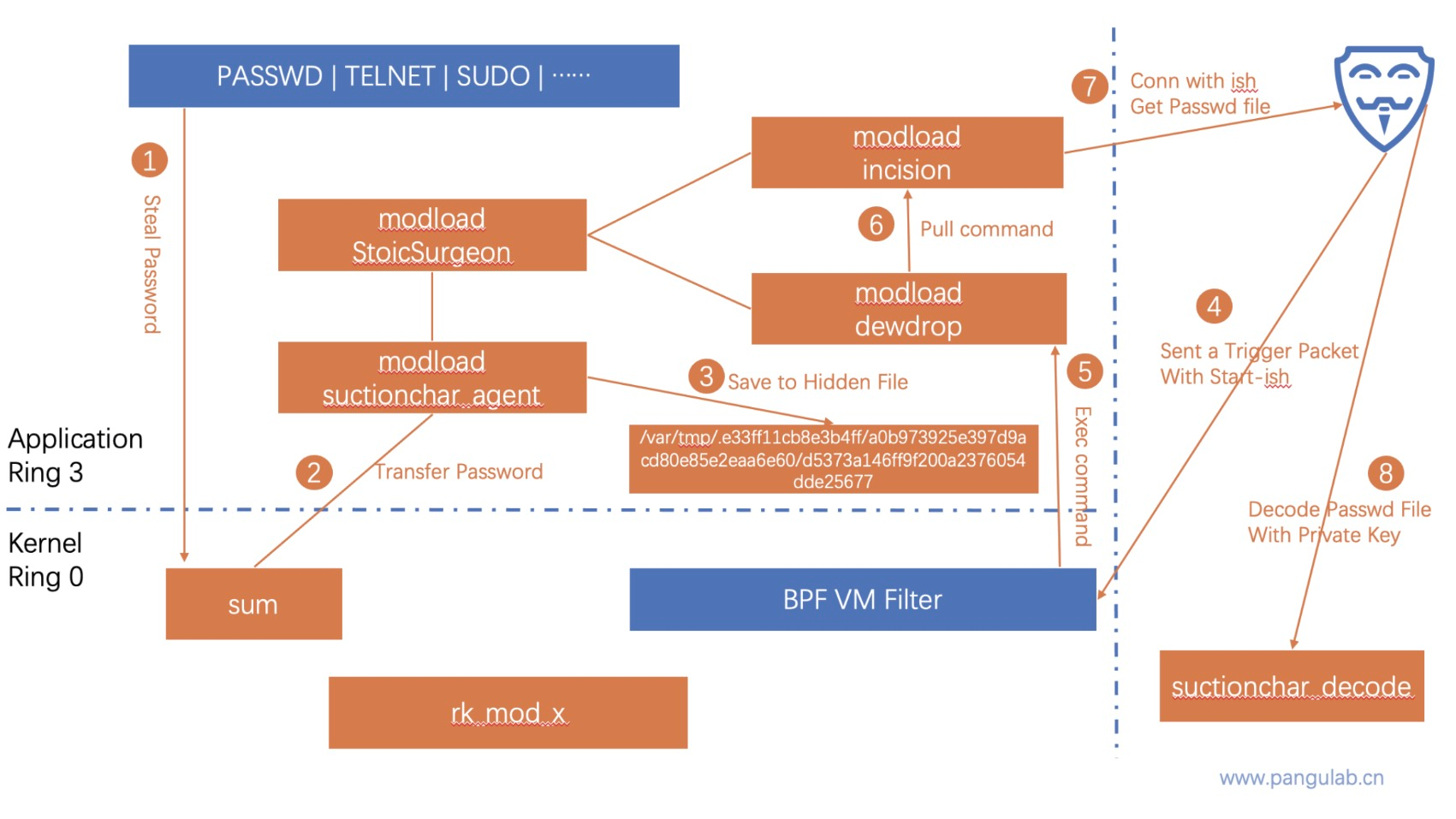
An illustration of cyberattack scenario flow of the Bvp47. /Pangu Lab
An illustration of cyberattack scenario flow of the Bvp47. /Pangu Lab
Highly stealthy, adaptable 'Suctionchar'
Being highly stealthy and adaptable, "Suctionchar" mainly targets Unix and Linux platforms, and it can steal accounts and passwords of a variety of remote management and file transfer services on target servers, said the report.
Technical analysis shows that "Suctionchar" can effectively work with other cyber weapons deployed by the NSA, CVERC cited experts on cybersecurity as saying.
"Suctionchar" can be delivered by the TAO to target servers with the help of the "Acid Fox" vulnerability attack weapon platform, the NOPEN Trojan and other cyber weapons featuring vulnerability attacks and persistent control over infected devices, experts noted.
It is found that "Suctionchar" can run stealthily on target servers, monitor in real time users' input on the terminal program of the operating system console, and intercept all kinds of user names and passwords.
Once obtained by the TAO, these user names and passwords can be used to access other servers and network devices to steal files or deliver other cyber weapons, the experts said.
In the TAO's cyberattacks against the Chinese university, "Suctionchar" was found to have worked together with other components of the Bvp47 Trojan program, a top-tier weapon of the hacking Equation Group of the NSA.
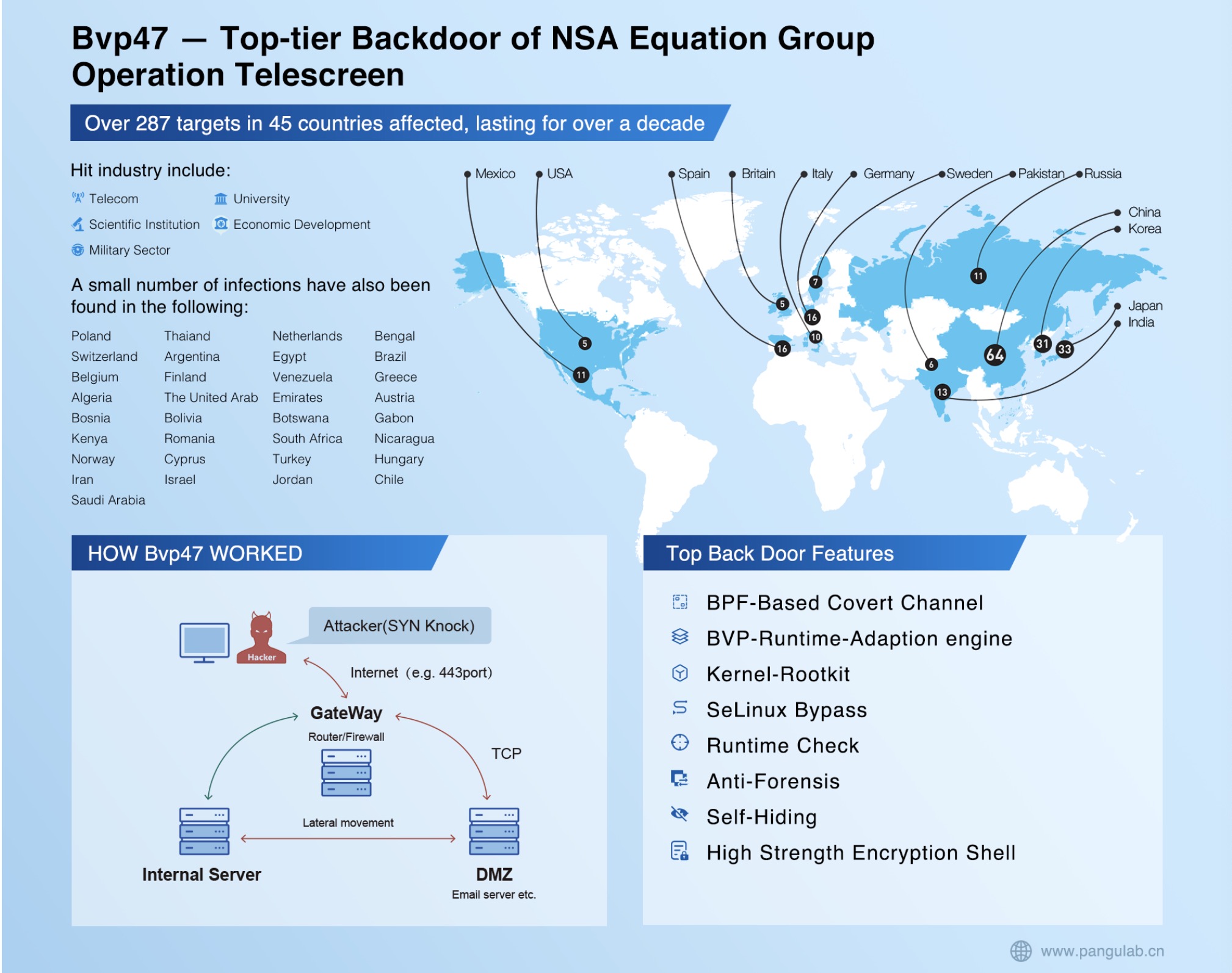
Infographics of top-tier backdoor of NSA equation group operation telescreen. /Pangu Lab
Infographics of top-tier backdoor of NSA equation group operation telescreen. /Pangu Lab
U.S. decade-long global cyberattacks
According to a previous report released by the Pangu Laboratory, the Bvp47 has been deployed to hit targets in 45 countries and regions around the world over a time span of more than 10 years.
The U.S. has launched indiscriminate cyberattacks around the world, rather than selectively targeting countries it deems strategic competitors, the Pangu Laboratory said.
Sixty-four systems in China were hacked by the Bvp47, making the country the biggest victim of the latest exposed cyberattacks, followed by 32 systems in Japan, 30 in the Republic of Korea and 16 in Germany, according to the lab.
Read More:
U.S. hacked China 10,000 times, stole 140GB of critical data: Report
China makes solemn representations to U.S. on university cyber attack
(With input from Xinhua)

